Rdp Cisco Anyconnect
- Cisco Anyconnect Remote Desktop
- Rdp Cisco Anyconnect Client
- Cisco Anyconnect Vpn Remote Desktop
- Cisco Anyconnect Windows 10
- Cisco Anyconnect Download
The problem was that every time when I tried to connect via Cisco AnyConnect Client it kept looping through the connection and never made it connect. The fix is quite simple actually, go to Network Connections from Control Panel, right-click Cisco AnyConnect Security Mobility Client Connection, and choose Properties. I am using a Cisco AnyConnect VPN for work and its holding up good, its dropped and auto reconnected once today so far. I have held video calls, conference calls, shared screens, RDP'ed, everything is working exactly as it was on my other provider without latency or other issues.
Some VPNs allow split tunneling, however, Cisco AnyConnect and many other solutions offer a way for network administrators to forbid this. When that happens, connecting to the VPN seals off the client from the rest of the LAN. Mad experiments: escape room - supporter edition download free. As it turns out, breaking this seal is not that hard, which can be useful for special cases like performing pentests over a VPN designed for average users.
In our case, we had to use a hardware token that only had drivers for Windows and Mac, while most of our tools run best (and are already installed) on Linux. We started investigating on both supported platforms mentioned above and found
what others have already discovered: the routing table is modified (and kept in this state), while packets are further filtered, probably using kernel hooks.
Both IPv4 and IPv6 are affected by this filtering, and traffic towards additional network interfaces also got redirected. So we embarked on a quest to find what could be done within the rules imposed by the VPN vendor. Our first stop was the gateway in our LAN towards the internet – and thus towards the VPN concentrator. The VPN client explicitly installed routes to keep that reachable, however, packets sent directly towards the LAN gateway never arrived there, leading us towards the idea of further kernel-based filters.
The next idea was the VPN server itself since it had to be able to receive packets from the clients as part of normal operation. However, the question is: how can you tell the packets apart on the gateway – as you still have to forward packets that are part of the normal VPN operator towards the VPN server. The trivial way was TCP port numbers, so we tried connecting to various TCP ports on the VPN server, but the gateway saw no SYN packets.
This left us with a single opportunity: keeping even the TCP port the same as the port used by the tunnel already. As netstat has shown, a TCP connection towards port 443 was kept open throughout the VPN session, and subsequent connections were allowed by the
filtering mentioned above – we could even see these SYN packets on the gateway. The only problem was to tell TCP streams apart at the gateway so that the VPN still worked while we could initiate connections outside of it at the same time.
And then it clicked: while trying to cope with the fact that many public (or semi-public) Wi-Fi networks filter everything besides TCP/443 (HTTPS), we had SSLH deployed to multiplex HTTPS and SSH on the same TCP port. This works reliably because they are really easy to tell apart upon the first packet:
- SSH clients send plain text one-liners that identify the protocol and client version, while
- SSL/TLS clients send binary Client Hello packets that identify the protocol version and supported ciphers.
SSH fits this case since its port forwarding features makes it possible to punch as many holes as necessary, regardless of the direction (VPN to LAN vs. LAN to VPN).
On Debian and its derivative systems, SSLH can be installed simply from the package with the same name (sslh) and configuration can be found in the file /etc/default/sslh as a command line, as this is where SSLH takes its options from. Below is the significant line:
Sonos S1 Controller App. The Sonos S1 Controller app lets you control Sonos systems with products that are not compatible with S2. By installation and/or use of the Sonos desktop controller, you are.  Sonos Desktop Controller App for Mac with OSX 10.7.5. The Desktop Controller App for Mac provided on the Sonos site doesn't support OSX 10.7.5. Any way to link my itunes? I downloaded the sonos Desktop Controller but when I try to open it, it says You can't use this version of the application Sonos with this version of Mac OS X.this application requires OS X 10.10 or later. The updated app makes it even simpler for you to search for content, control the sound, and personalize your listening experience with new features like saved room groups. Increased security Enhanced protocols, including support for elliptic curve cipher suites in SSL/TLS, keep your system safer and your data more secure.
Sonos Desktop Controller App for Mac with OSX 10.7.5. The Desktop Controller App for Mac provided on the Sonos site doesn't support OSX 10.7.5. Any way to link my itunes? I downloaded the sonos Desktop Controller but when I try to open it, it says You can't use this version of the application Sonos with this version of Mac OS X.this application requires OS X 10.10 or later. The updated app makes it even simpler for you to search for content, control the sound, and personalize your listening experience with new features like saved room groups. Increased security Enhanced protocols, including support for elliptic curve cipher suites in SSL/TLS, keep your system safer and your data more secure.
This just means that SSLH listens on the internal (LAN) IP address of the gateway and based on the first packet received from a client that reaches this port, it either forwards it to
- a local SSH server (here we had the VPN client running on a Windows VM, and the Linux host had the SSH daemon running, hence the variable name
$VM_HOST_IP) or - the original VPN server.
Changes to the options can be applied under Debian and its derivatives by running /etc/init.d/sslh restart and the results can be tested in isolation first by connecting to TCP port 443 of the gateway, which should behave like the VPN server when using a TLS client like openssl s_client and act as an SSH server when using OpenSSH or PuTTY.
When all this works, the last bit is to redirect traffic towards the VPN server to SSLH. One way is using NAT functionality from iptables:
This command adds a rule to the chain called PREROUTING within the nat table, where packets arrive before the routing decision happens. The next part is the filter, which is important to avoid loops: we only apply the magic to packets where the network interface that the packet arrives through is the LAN interface. The rest narrows the filter further to the destination TCP port being 443 and the destination host being the VPN server. The last part is what happens when this rule matches: we invoke the REDIRECT target that rewrites
- the destination host to the IP address of the interface the packet arrived through (here: LAN interface) and
- the destination port to the one supplied (here: 443).
Since SSLH was configured to listen on TCP port 443 on the LAN interface, this results in the same effect as in the above SSLH testing scenario, where we connected directly to TCP port 443 on the gateway. And the best part is that the NAT solution provided by iptables is fully bidirectional, reply packets from SSLH are automatically translated back to make it seems as if they were sent by the VPN server.
So with the iptables rule in place, everything is ready for a real-life test. The progress of SSLH can be followed in syslog and as it can be seen below, after the AnyConnect client has connected properly, SSH connections can also get through, and everything gets routed to its proper destination.
Objective
Remote Desktop Protocol (RDP), is a proprietary protocol developed by Microsoft, which provides a user with a graphical interface to another computer. Every Windows version beginning with Windows XP includes an installed Remote Desktop Connection.
The objective of this document is to explain how to configure Remote Desktop Connection between two systems. To access a remote desktop connection you need to establish a VPN Tunnel between two routers. To establish VPN Tunnel between two routers, choose VPN > IPSec > Basic VPN Setup.

Applicable Devices
• RV220W
• RV120W
Configure Remote Desktop Protocol
The following explains how to configure RDP.
Configuration on the Routers
Note: Complete Steps 1-9 for both your router and the remote router.
Step 1. Use the web configuration utility to choose Firewall > Access Rules. The Access Rules page opens:
Step 2. To create new RDP firewall rule click Add Rule. ADD/Edit Access Rule Configuration page opens:
Note: To learn more about configuration of firewall access rules in detail please refer to Access Rules Configuration RV120W and RV220W.
Step 3. Choose Inbound(WAN (Internet) > LAN (Local Network)) from Connection Type drop down list.

Step 4. Based on your requirements you can choose the required action from the Action drop down list, but don't choose the always block option, because it blocks the service connection. You can configure schedules to allow a particular action using the Configure Schedules button.
Step 5. Choose RDP service from the Service drop down list. If the RDP service is not present on the Service drop down list, then click Configure Services or choose Firewall > Advanced Settings > Custom Services to configure RDP.
Step 6. Choose the required Source IP option for your network from the Source IP drop down list. In this scenario source IP ANY is used, so there is no need to specify start and finish IP addresses.
Step 7. Enter the Local IP address of the server in the Send to Local Server (DNAT IP) field.
Step 8. Choose Enabled from Rule Status drop down list.
Cisco Anyconnect Remote Desktop
Note: Follow the same procedure for outbound traffic. But choose Connection Type Outbound (LAN (Local Network) > WAN (Internet)) from the Connection Type drop down list and choose destination IP based on your requirement from the Destination IP drop down list. In this scenario Destination IP ANY is used.
Step 9. Click Save to save the settings. The configured RDP rule appears on the Access Rule Table.
Configuration on Desktops
Rdp Cisco Anyconnect Client
Note: Follow steps 1-4 for the computer you want to access remote desktop connection, and steps 5-9 are for the computer you are accessing from.
Step 1. Click the Start Menu of your computer and right click on the Computer tab.
Step 2. Choose Properties > Remote Settings > Remote. The System Properties page opens:

Cisco Anyconnect Vpn Remote Desktop
Step 3. Click the checkbox to Allow Remote Assistance connections to this computer.
Step 4. Click OK. This enables remote desktop connections to your computer.
Cisco Anyconnect Windows 10
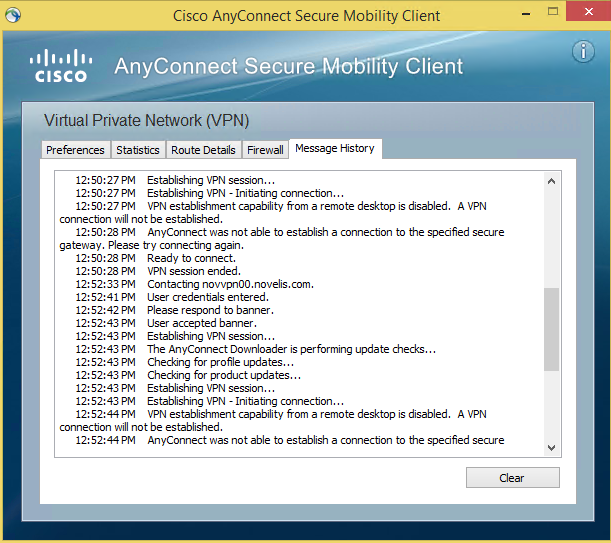
Step 5. Click the Start Menu of your computer and choose All Programs > Accessories > Remote Desktop Connection. The Remote Desktop Connection Window opens:
Step 6. In the Computer field enter the IP address of the remote computer, whose desktop you want to access.
Step 7. Click Connect.
Step 8. Click Yes.
Cisco Anyconnect Download
The Log On to Windows page of the remote desktop opens:
Step 9. If the connection is established, then the window asks for the username and password of the remote computer. Enter the user name and password in the Username and Password fields respectively. The remote desktop then opens:
If the connection is not established then it shows the error window as below:

